CS3340: Intro OOP and Design |
||||||
|
Speech Verification
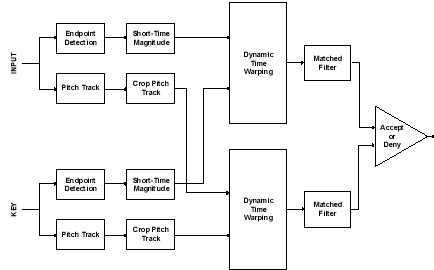
This system is some work done out of Rice University and implements a Simple Verification Process after speaker has trained system with password.
|
Data collection
|
|
Endpoint Detection
|
|
Rate Adjustment to Speaker's Stored Password Signal
|
|
Filtering to Compare Input Signal and Speaker's Stored Password Signal
|
|
Results on a very SMALL sample (4 people):
|